
Texas Business Software has been designed for multi-user distributed concurrent access and has been implemented with a true real world securlty model. The Texas Security Modle implements a hierarchical permission structure (as seen below) where users belonging to a permissions group above have the ability to control the users below.
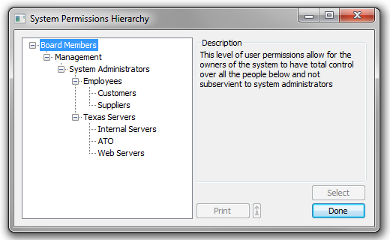
This hierarchical model gives system owners the ability to control the functionality of users by controlling which methods a user may access. For example the floor managerial staff may have permission to add, edit and delete system orders, while normal service staff would only have permission to add and edit system orders. This security model also prevents some users from accessing sensitive information - such as personal employee information like payroll or medical information.


